Automated security
for every purpose
Secure your applications and networks with the industry’s only vulnerability management platform to combine XDR, SAST, DAST and mobile security.
Trusted by over 3,200 customers in 100+ countries




























The market has spoken
SC Labs Reviews
SC Magazine





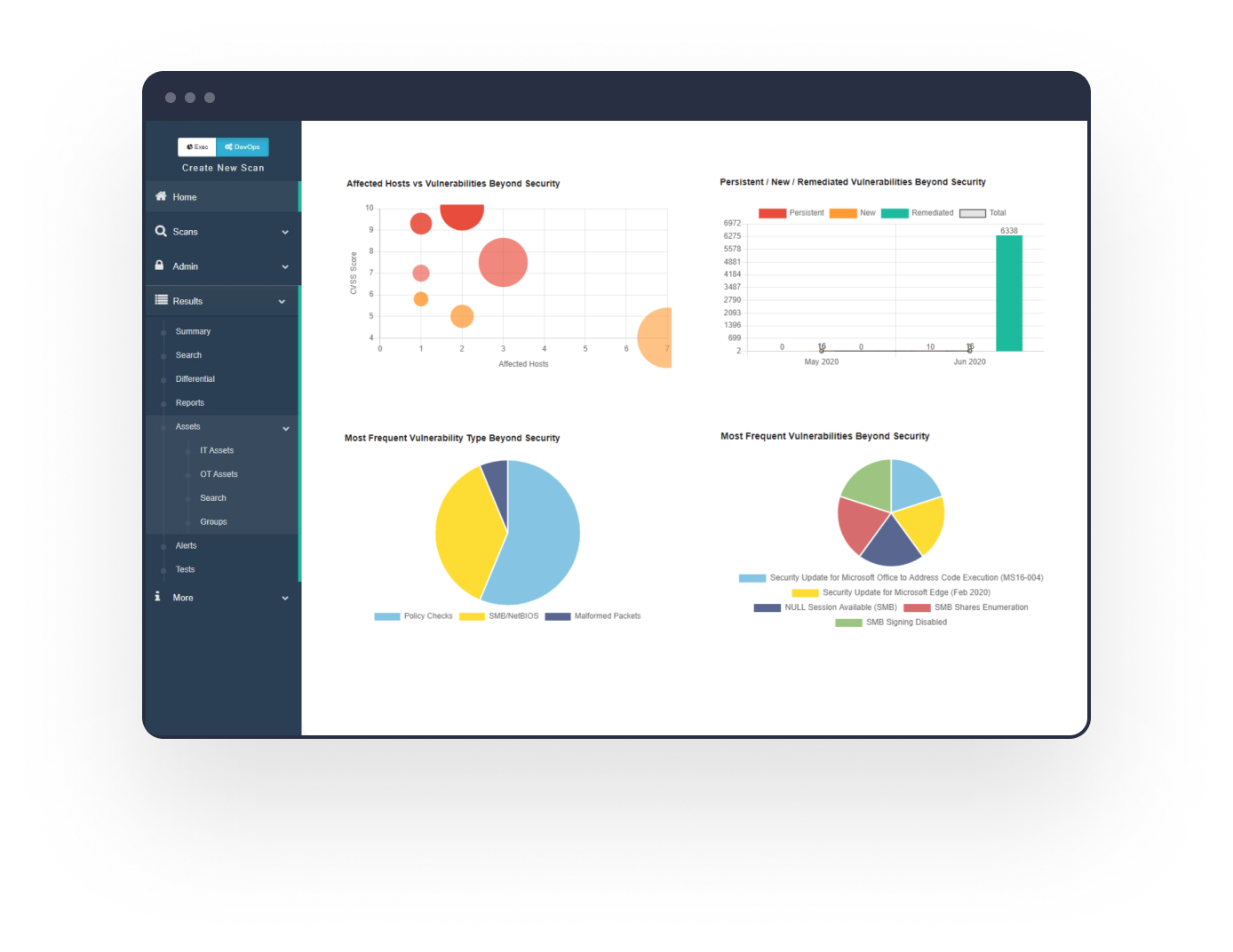
- 4.75/5
Beyond Security beSECURE is a solid vulnerability management solution with robust automation capabilities and one-click integrations, reducing the manual effort security teams otherwise must put forth and allowing them to focus on remediation instead.
Reduce complexity with connected solutions
compliance solutions for IT, OT and IoT environments.
Use ML-driven intelligence to see anything coming your way and proactively respond to today’s risks to your networks, endpoints and cloud-based systems.
Find vulnerabilities and flaws early in the software development life cycle (SDLC) with automated source code scanning that scales as you build.
Why businesses trust Beyond Security
99%
Alert Noise
Reduction
60%
Reduced
Costs
142%
Increase in
Asset Coverage
What our customers have to say
Recommended for you







Want to see Beyond Security in action?
Certifications
Software Security Testing
PCI Information
Copyright © 2020 Beyond Security. All Rights Reserved.



























